Unveiling the Intricacies of Worm Maps: A Comprehensive Exploration
Related Articles: Unveiling the Intricacies of Worm Maps: A Comprehensive Exploration
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Intricacies of Worm Maps: A Comprehensive Exploration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Intricacies of Worm Maps: A Comprehensive Exploration
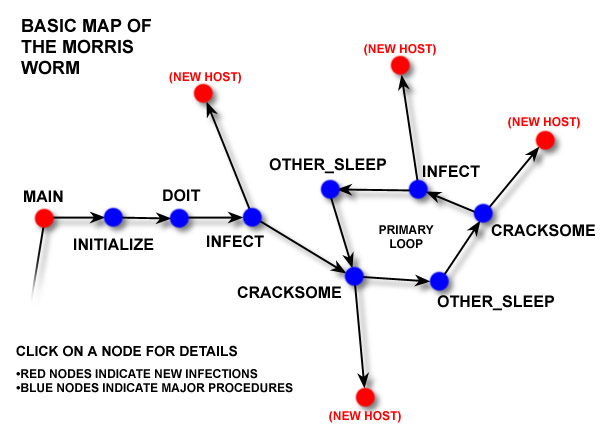
The concept of a "worm map" might conjure images of subterranean tunnels or intricate patterns woven by earthworms. However, in the realm of cybersecurity, "worm map" takes on a different, albeit equally fascinating, meaning. It refers to a visual representation of the spread and impact of a computer worm, a malicious program designed to replicate itself and spread across networks.
Understanding the intricacies of worm maps is crucial for cybersecurity professionals, network administrators, and anyone concerned with safeguarding their digital assets. This article delves into the core concepts of worm maps, exploring their construction, benefits, and applications in the battle against cyber threats.
The Genesis of Worm Maps
Worm maps are a relatively recent development in cybersecurity, arising from the need to visualize and comprehend the complex propagation patterns of computer worms. These maps serve as a crucial tool for analysts to gain valuable insights into the spread of malware, enabling them to identify key vulnerabilities, predict future attack vectors, and develop effective mitigation strategies.
Building a Worm Map: A Layered Approach
Creating a comprehensive worm map involves a multi-layered approach, encompassing various data sources and analytical techniques. Here’s a breakdown of the key elements:
-
Data Collection: The foundation of any effective worm map lies in the collection of relevant data. This includes:
- Network Traffic Analysis: Analyzing network traffic patterns can reveal the movement of worm-infected systems, identifying source and destination nodes.
- Log Analysis: Examining system logs provides valuable information about the worm’s behavior, including timestamps of infection, files accessed, and network connections established.
- Vulnerability Scans: Identifying vulnerable systems within a network helps pinpoint potential entry points for the worm.
- Threat Intelligence: Gathering information from security researchers, threat intelligence feeds, and industry reports provides insights into the worm’s characteristics, propagation mechanisms, and known attack vectors.
-
Data Visualization: Once collected, the data needs to be visualized in a meaningful way. This is where worm maps come into play. Various visualization techniques can be employed, including:
- Network Graphs: These maps depict the interconnectedness of systems within a network, highlighting the spread of the worm.
- Timelines: Visualizing the progression of the worm’s infection over time helps track its spread and identify key milestones.
- Heatmaps: These maps use color gradients to indicate the intensity of infection across different parts of the network, offering a visual representation of the most affected areas.
-
Analysis and Interpretation: The final stage involves analyzing the data presented on the worm map to draw meaningful conclusions. This includes:
- Identifying the Root Cause: Analyzing the worm’s initial entry point and propagation path helps determine the root cause of the infection.
- Identifying Vulnerable Systems: Identifying systems with high infection rates or potential for further spread highlights vulnerable areas that require immediate attention.
- Predicting Future Spread: Analyzing the worm’s behavior and propagation patterns can help predict future attack vectors and vulnerable systems.
Benefits of Worm Maps: A Strategic Advantage
The strategic advantages of using worm maps in cybersecurity are manifold:
- Enhanced Situational Awareness: Worm maps provide a clear and comprehensive picture of the current threat landscape, enabling security teams to understand the scope and impact of the worm infection.
- Improved Response Time: By quickly visualizing the spread of the worm, security teams can rapidly identify critical systems and implement appropriate containment measures.
- Targeted Mitigation Strategies: Worm maps facilitate the development of targeted mitigation strategies, focusing resources on the most vulnerable areas and critical systems.
- Proactive Security Measures: Analyzing the worm’s behavior and propagation patterns allows for proactive security measures, such as patching vulnerabilities and implementing stricter access controls.
- Post-Incident Analysis: Worm maps provide valuable insights for post-incident analysis, enabling security teams to identify weaknesses in their defenses and improve their overall security posture.
Applications of Worm Maps: A Multifaceted Tool
Worm maps find applications in various cybersecurity scenarios, including:
- Incident Response: During a worm outbreak, worm maps are invaluable for tracking the spread of the infection, identifying vulnerable systems, and implementing containment measures.
- Vulnerability Assessment: Worm maps can help identify potential vulnerabilities that could be exploited by worms, enabling security teams to prioritize patching efforts.
- Threat Intelligence: Analyzing worm maps can provide valuable insights into the tactics, techniques, and procedures (TTPs) employed by attackers, improving threat intelligence gathering.
- Security Awareness Training: Worm maps can be used to illustrate the potential impact of worm infections, raising awareness among users about cybersecurity best practices.
- Research and Development: Worm maps are essential tools for researchers studying malware behavior and developing new security solutions.
FAQs on Worm Maps: Addressing Common Questions
Q: What are the different types of worm maps?
A: Worm maps can be categorized based on their visualization techniques, data sources, and intended purpose. Common types include network graphs, timelines, heatmaps, and interactive maps.
Q: What are the limitations of worm maps?
A: While powerful tools, worm maps have limitations. They rely on accurate data collection and analysis, and their effectiveness depends on the sophistication of the worm and the complexity of the network.
Q: How can I create a worm map?
A: Creating a worm map requires specialized tools and expertise in data collection, analysis, and visualization. Many security information and event management (SIEM) systems and network security monitoring (NSM) tools offer features for creating worm maps.
Q: How can I use worm maps to improve my cybersecurity posture?
A: By analyzing worm maps, you can identify vulnerable systems, implement appropriate security controls, and develop effective mitigation strategies to prevent future worm infections.
Tips for Utilizing Worm Maps Effectively
- Choose the right visualization technique: Select a visualization technique that best suits the data and intended purpose of the map.
- Ensure accurate data collection: Accurate data collection is crucial for the effectiveness of worm maps.
- Use appropriate tools and techniques: Utilize specialized tools and techniques for data analysis and visualization.
- Regularly update and refine maps: Worm maps should be regularly updated and refined based on new data and insights.
- Integrate with other security tools: Integrate worm maps with other security tools for a comprehensive security posture.
Conclusion: Worm Maps – A Vital Tool in the Cybersecurity Arsenal
Worm maps have emerged as a vital tool in the fight against cyber threats. Their ability to visualize the complex propagation patterns of computer worms provides invaluable insights for security professionals, enabling them to make informed decisions, implement effective mitigation strategies, and ultimately enhance their cybersecurity posture. As the threat landscape continues to evolve, worm maps will play an increasingly important role in protecting our digital world.






Closure
Thus, we hope this article has provided valuable insights into Unveiling the Intricacies of Worm Maps: A Comprehensive Exploration. We thank you for taking the time to read this article. See you in our next article!